-
- Setup a Stack (Cluster)
- Setup Hosting Plans
- Setup a Site
- Apply changes from Idealstack to AWS
- Create & manage databases
- Upload files using SFTP or the web based file manager
- Viewing logs
- Troubleshooting
- Connect to your site with SSH
- Managed Security Updates
- Deleting a stack
- Setting up SES for email delivery
Connecting shared resources in another VPC to Idealstack
Sometimes you want to connect shared resources, such as EC2, RDS, Elasticache or ElasticSearch to multiple Idealstack stacks, or connect Idealstack to resources you already have. How you do this depends on what type of service it is:
- Some services are accessed exclusively over AWS API's over the cloud - examples of these are S3, DynamoDB, SQS etc. For services like this, you can securely connect them to your Idealstack site via IAM Policies
- Many other services use network security to provide access control. This includes any type of service that requires a VPC when you create it - examples are EC2, RDS and Elasticache
Idealstack creates it’s own Virtual Private Cloud to isolate sites from the rest of your AWS infrastructure - but you can connect this to your own VPC using a VPC Peering connection. You can also VPC peer with VPC's in other regions or even other AWS accounts
These steps are required for AWS resources that use network-based security, for instance EC2, RDS, Elasticache, Elasticsearch. Some AWS services such as S3 or DynamoDB are purely internet-based services and do not require a VPC to operate, for those types of resources these steps aren't required - instead you should setup an IAM role to allow access and attach that to your site.
Create a VPC (skip if you already have one)
You should skip this if you already have a VPC you want to use.
See also the AWS docs for more information about VPC's. The key things you need to make sure of with your VPC's should be that:
- They must use a non-overlapping IP range. Idealstack creates it's VPC's using sequential networks starting at 10.10.0.0/16, so the second stack will be 10.11.0.0/16, the third will be 10.12.0.0/16 and so forth. So you can use lower numbered networks (eg 10.9.0.0/16) or addresses in other private ranges such as 192.168.12.0/24 or 172.16.4.0/24 that don't overlap this
- You should probably create them on the same availability zones (idealstack uses two, eg ap-southeast-2a and ap-southeast-2b), to minimize inter-AZ traffic charges. This isn't essential though and VPC peering can even happen between AWS regions and different AWS accounts.
The instructions below show how to create a minimal VPC:
-
Go to VPC in the AWS console
-
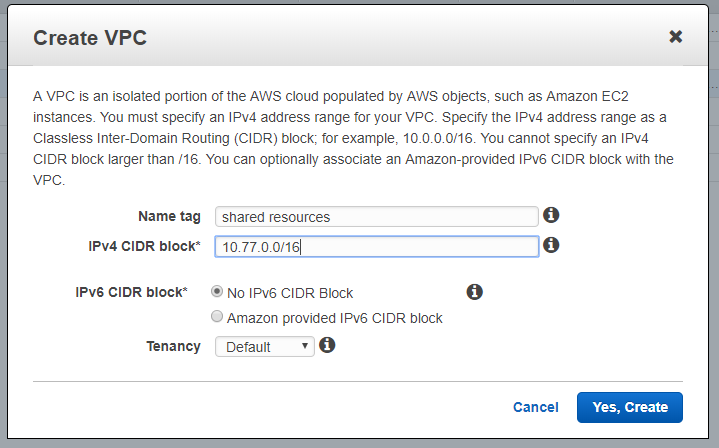
Create a VPC. Give it a different IP range from your hosting cluster. Idealstack assigns IP ranges sequentially from 10.10.0.0/16, 10.11.0.0 and so forth. So ideally give your VPC a range in the , or much higher, eg 128, to remain safe. HINT : avoid common subnets like 10.1.0.0/16, as there’s less chances of clashes between ranges.
-
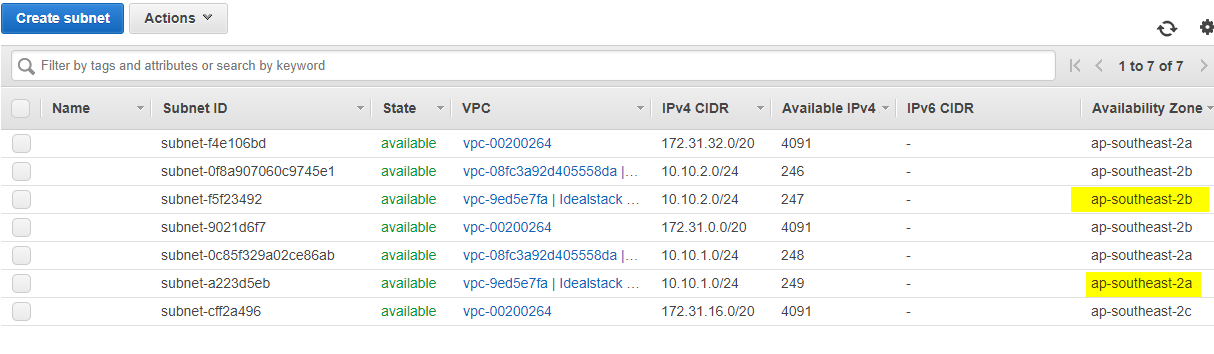
Create two subnets in this VPC. Use the same AZ’s as the idealstack network: in this case ap-southeast-2a and ap-southeast-2b
-
Give it a CIDR of *.1.0/24 and *.2.0/24
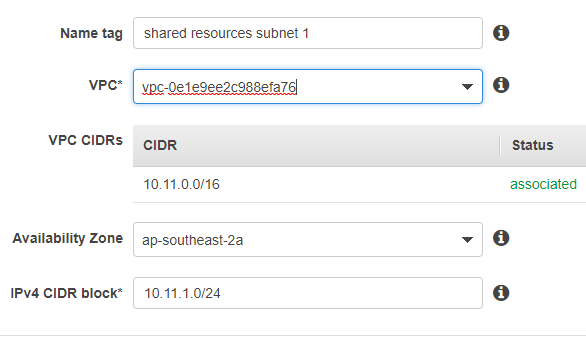
You might also need to add a NAT gateway to the VPC if you want resources in it to connect to the internet.
Setup VPC peering
-
Go to Peering Connections in the VPC menu and click Create
-
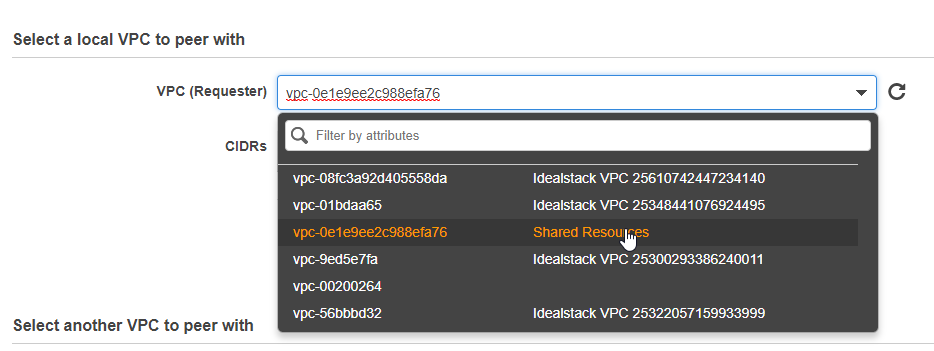
For VPC(Requester) choose the new VPC you created above
-
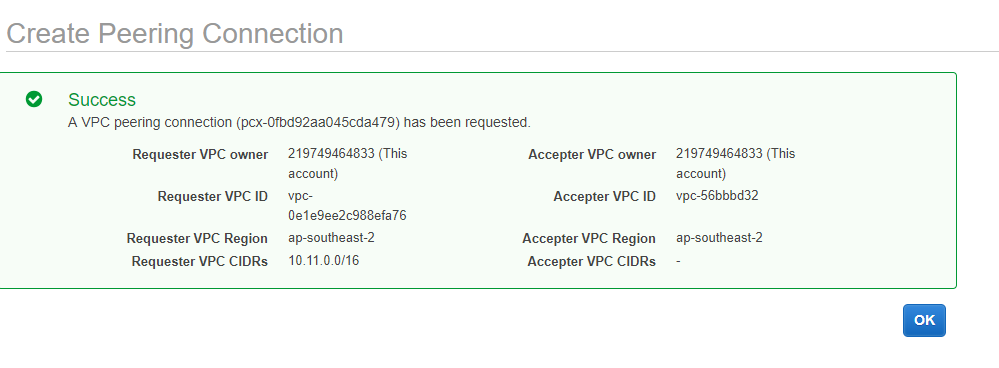
For VPC (Acceptor) choose the Idealstack VPC
-
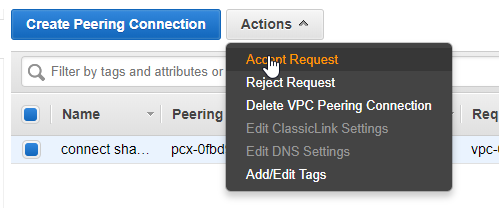
Now you have to accept the peering request. Select it in the list and choose Accept Request from the actions
-
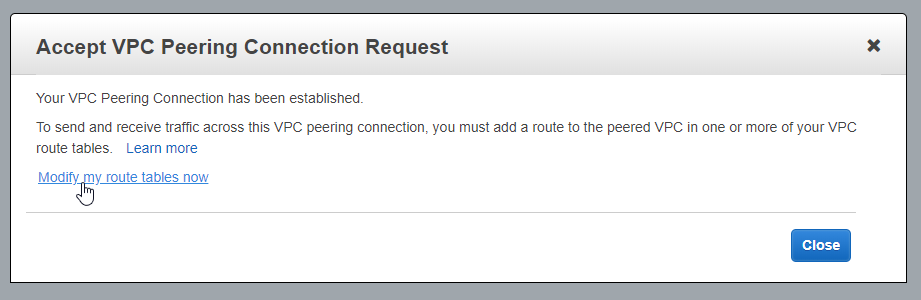
Once accepted you’ll see this screen. Choose “Modify my route tables now”
-
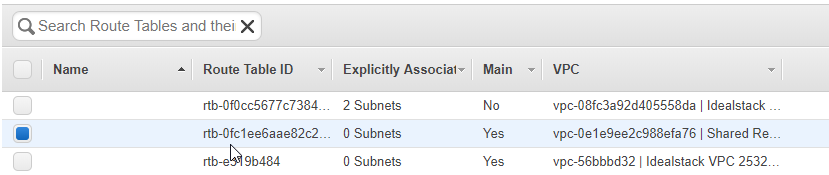
Edit the routing table for your shared VPC:
-
Click on it in the list:
-
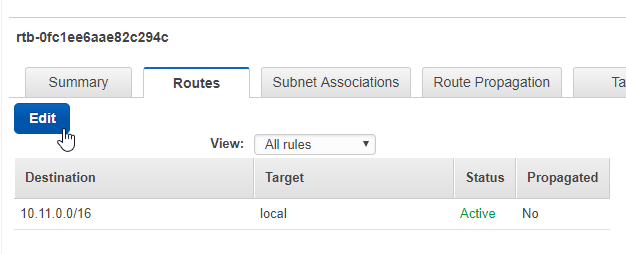
Click on Routes:
-
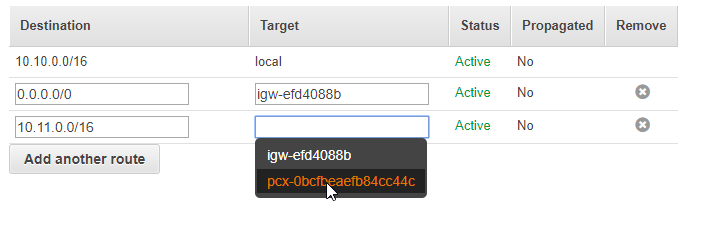
Enter the IP range of the Idealstack VPC and select the Peering connection as the target
-
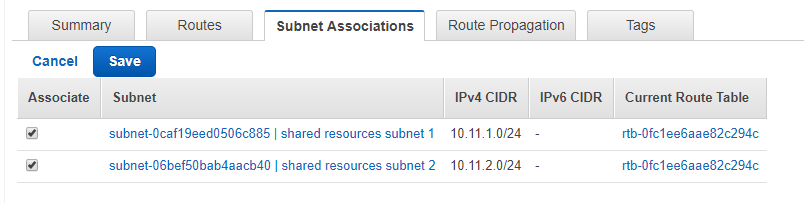
Ensure this route table is associated with both subnets of your VPC under Subnet Associations
-
Also edit the Route table for the Idealstack VPC. Use the IP range of your shared VPC
-
Example: Create RDS in new VPC
Now you can create resources in this VPC and the Idealstack sites will be able to connect to them. In most cases the steps are:
- Create the resource in the shared VPC
- Edit it's security groups to allow the Idealstack networks (eg 10.10.0.0/16) to have access
These steps will work for any AWS resource that uses network-based security (eg RDS, Elasicache, ElasticSearch, EC2)
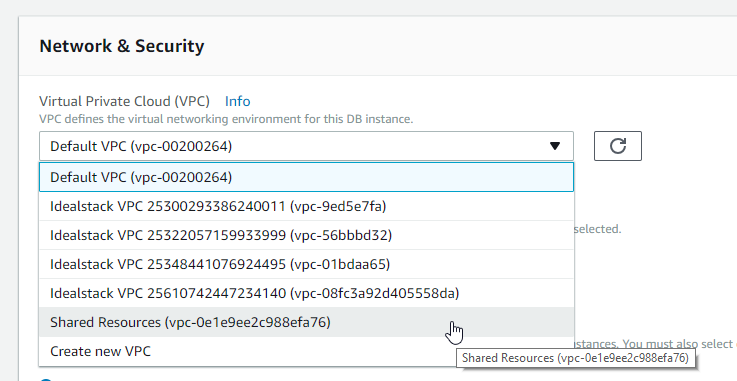
- When asked to enter a VPC choose your shared VPC
-
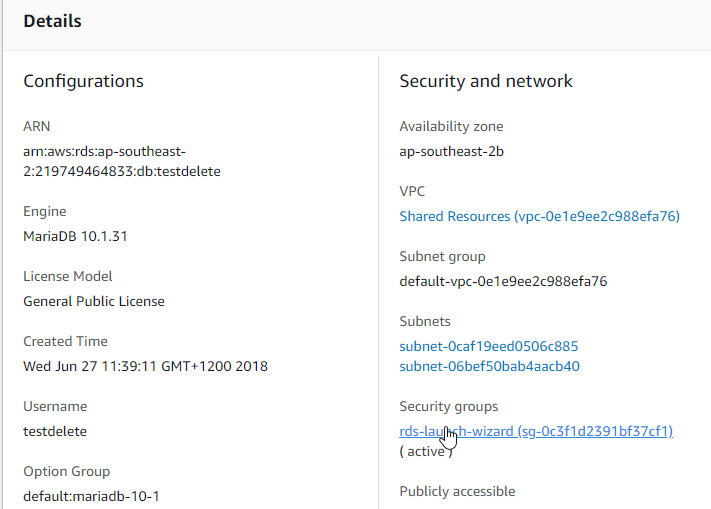
Wait for the instance to create. Then click it in the instances list and edit it’s security group
-
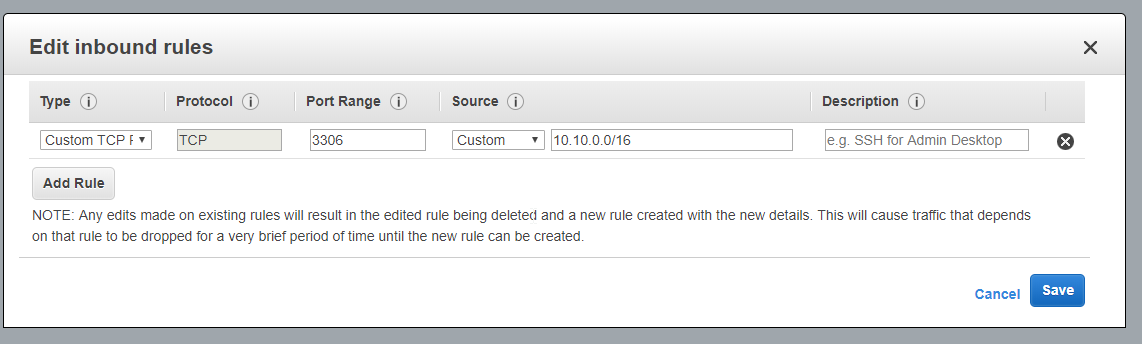
Add an inbound rule for the IP range of the Idealstack VPC
-
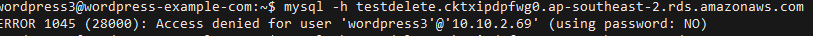
Now test it. SSH to one of your sites, and copy the Endpoint
-
Connect to this with the mysql client. It should say ‘Access Denied’ (rather than ‘Can’t connect’ or a hanging/timeout)