Codebuild for PHP - Speeding it up using caching, adding code coverage
Idealstack • January 15, 2018
configurationcol-sm-12">
This is part 2 of our series on using AWS Codebuild with PHP projects. You probably want to start with part 1.
In this article, we'll discuss speeding up our builds with caching, and generating a code coverage report using PHPUnit (you could use the same techniques to upload other code quality metrics from various other PHP code analysis tools too if you want)
As with the previous posts, we're using this Github repository https://github.com/Idealstack/codebuild-example - you can follow along by either making your own fork of this, or copy the relevent buildspec.yml files into your own project and tweak them appropriately
Speeding up codebuild using caching
Codebuild can cache data, which allows us to speed up the build. Since we're installing a lot of debian packages in our build it helps to cache the apt packages used by ubuntu to install PHP. Any PHP project can also probably benefit by caching composer packages. If you are using nodejs based tools like gulp or webpack in your build then caching the packages for that is another win.
Create an S3 bucket to store your cache. You can just accept all the defaults when creating the bucket
Edit your codebuild project
Change the ‘Cache’ setting to use S3
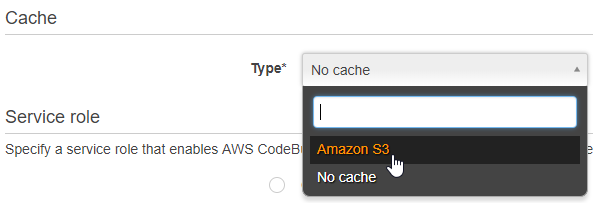
Choose your S3 bucket, then Save
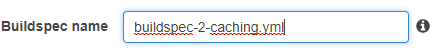
Use the build spec file codebuild-2-caching.yml
The first time you build after this, you’ll see it takes a while
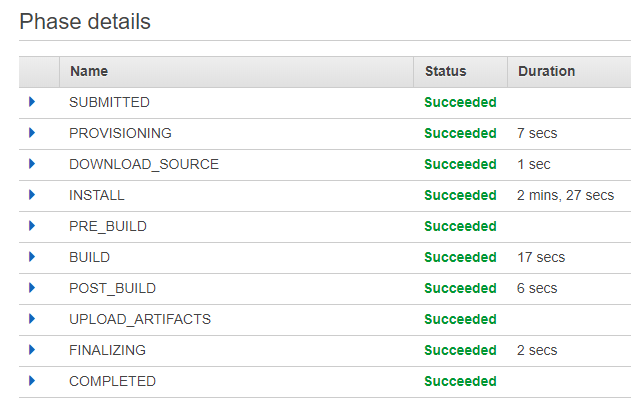
But in the build logs it’ll upload cache
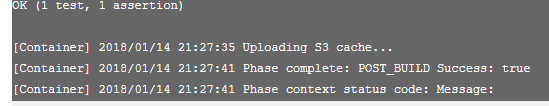
The next time you build, it will be faster:
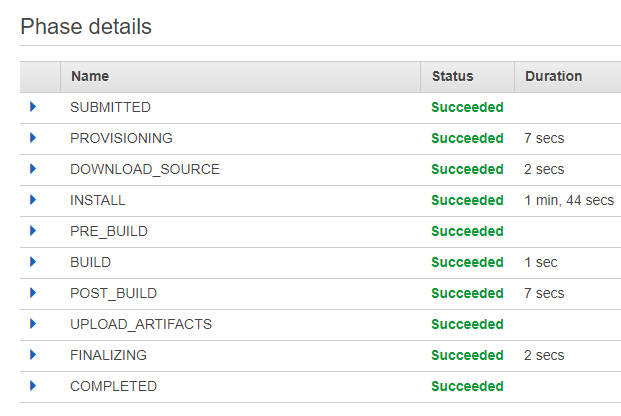
As you can see, the build takes about a third as long. And you should see in the logs that it uses cached files in composer, npm and apt-get install commands
Code coverage reports
PHPUnit can generate reports on the coverage of your unit tests. You probably want this to be generated automatically too, so that when you are code reviewing a commit or pull request you can know whether it has improved or worsened your code coverage.
To get an html report on code coverage from your builds, first create a new s3 bucket to hold the report. Then update your build specification to use buildspec-3-coverage.yml.
Edit your project, click to show Advanced Settings, and add an environment variable called COVERAGE_S3_BUCKET - set it to the name of the bucket you created above
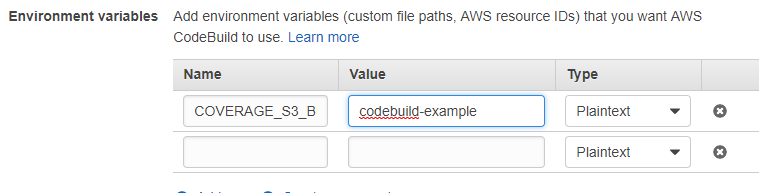
Also take note of the “Role Name”, which you’ll need in the next step
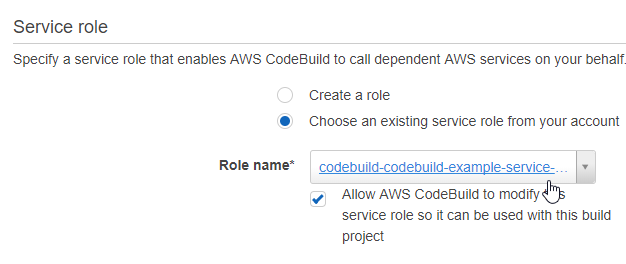
Now you need to give codebuild access to this s3 bucket. To do this you need to allow access to the IAM service role that codebuild creates
Go to IAM in the AWS “Services” menu
Go to “Roles” in the IAM menu

Find the role that codebuild is using
On the “Permissions” tab click “Add inline policy”
Go to the JSON tab and paste the following. Update the bucket name (in this example, codebuild-example-test)
{ "Version": "2012-10-17", "Statement": [ { "Sid": "CodebuildCoverageAccess", "Effect": "Allow", "Action": [ "s3:ListBucket", "s3:DeleteObject", "s3:PutObject" ], "Resource": [ "arn:aws:s3:::codebuild-example/*", "arn:aws:s3:::codebuild-example" ] } ] }
Click “Review Policy”, Give the policy a name eg “CodebuildCoverageS3Access” & click “Create policy”
Now when you rebuild your project you should see the coverage uploading
How to view this report? We don’t want to make the coverage report public - there’s potentially all sorts of security-sensitive information in there. The best solution we’ve found so far is to limit it by IP Address
- Go to the bucket in S3 & go to the permissions tab
- Click the Bucket policy button
- Paste in the policy: update the bucket name and IP and Save
{ "Version": "2012-10-17", "Id": "S3PolicyId1", "Statement": [ { "Sid": "IPAllow", "Effect": "Allow", "Principal": "*", "Action":["s3:GetObject"], "Resource": "arn:aws:s3:::examplebucket/*", "Condition": { "IpAddress": {"aws:SourceIp": "54.240.143.0/24"} } } ] }
Now you should be able to navigate to the index.html in the s3 bucket and click the link
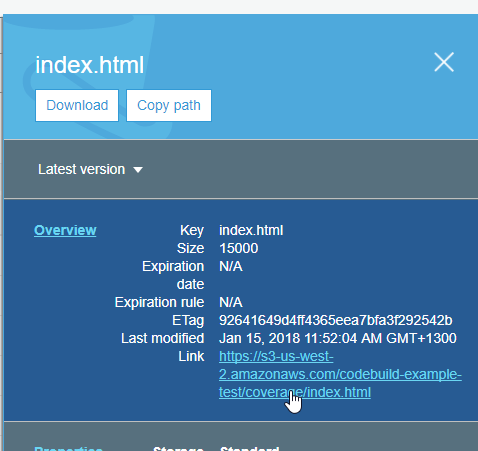
And view the coverage report
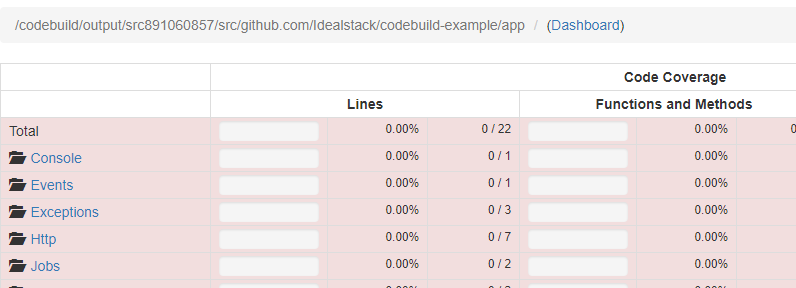
What's next?
In part 3 we'll show you how to deploy automatically over ssh
Harness the power of AWS for hosting PHP-based websites and apps.
Idealstack is a powerful hosting console that creates a modern, autoscaling,
best-practice, AWS-native hosting cluster for PHP-based code in your AWS account