Codebuild for PHP - Deploying using SFTP (to idealstack or any similar system)
Idealstack • January 15, 2018
configurationThis article is part of a series on setting up codebuild, so you might also want to check out part 1 and part 2 first.
Once you've got Codebuild building and testing your code, the obvious next step is to get it to deploy automatically when it passes tests - this is called Continuous Deployment.
Continuous Deployment is an intimidating concept when you first hear about it - surely you want to manually test your releases a little bit first before putting live?! But you have to ask yourself: how much do you really test each release. Once you have good unit tests in place, the chances are that you'll just release code as a formality, without any manual testing. In which case you might as well automate it. Put all the time you spent on manual testing into making better unit tests. If particular features need manual testing - make sure that is part of your code review process before you merge the changes.
In this article we'll show you how to upload files over SFTP and run some SSH commands to deploy your app - you should be able to easily adapt it to deploy any php app.
The challenge to implementing this in codebuild is to safely store your ssh key. You definitely don’t want to commit this into your repository in the buildspec.yml, or just throw in an S3 bucket and hope for the best. A safer approach is to use the AWS Systems Manager Parameter Store and encrypt the key using AWS KMS
As with the previous posts, we're using this Github repository https://github.com/Idealstack/codebuild-example - you can follow along by either making your own fork of this, or copy the relevent buildspec.yml files into your own project and tweak them appropriately
Go to AWS Systems Manager
In the AWS Systems Manager menu, choose Parameter Store
Create a parameter
Give the parameter a sensible name, description, and choose the type to be SecureString
Generate an SSH private key, and paste it into the value field
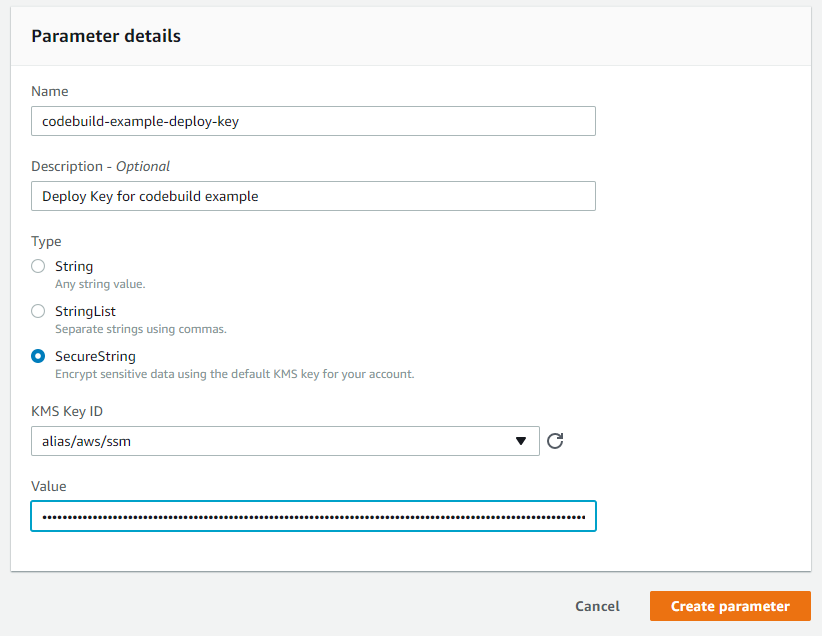
Paste in the SSH private key. You should generate a unique key for every project, one that only has access to your hosting server - don't just use the same SSH key you use for your everyday use here.
Now you need to give codebuild access to this s3 bucket. To do this you need to allow access to the IAM service role that codebuild creates
Go to IAM in the AWS “Services” menu
Go to “Roles” in the IAM menu

Find the role that codebuild is using
On the “Permissions” tab click “Add inline policy”
Go to the JSON tab and paste the following. Update the name of the key (in this example, codebuild-example-deploy-key)
{ "Version": "2012-10-17", "Statement": [ { "Sid": "CodebuildAccessDeployKey", "Effect": "Allow", "Action": "ssm:GetParameters", "Resource": "arn:aws:ssm:*:*:parameter/codebuild-example-deploy-key" } ] }Click “Review Policy”, Give the policy a name eg “CodebuildAccessDeployKey” & click “Create policy”
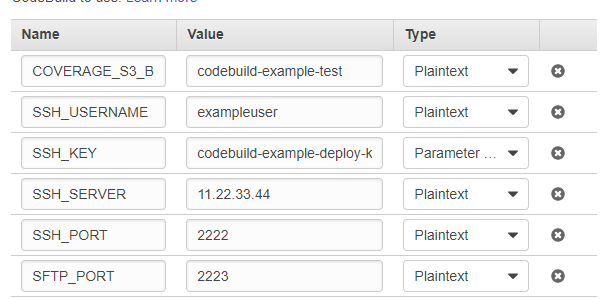
Edit the codebuild project and add environment variables - SSH_SERVER, SFTP_PORT, SSH_PORT, SFTP_PORT, SSH_USERNAME referring to the ports, username and server IP addresses of your SFTP/SSH server. Then add a variable called SSH_KEY, choose the type to be Parameter Store with the name of the encrypted parameter you created above
Add this code to the post_build section of your buildspec.yml.
# Deployment to the SFTP server - bash ./codebuild-deploy.shThe real work happens in codebuild-deploy.sh - You'll want to tweak the directories copied and the remote commands needed depending on your own project.
What could you tweak or change here?
We've tried to keep this example generic, but in real world projects there's a couple of things you might want to do differently
- Consider using Deployer for more sophisticated zero-downtime deployments.
- If instead of deploying over SSH/SFTP you've got more complex deployment requirements on EC2/ECS etc, AWS Code Pipeline is the right AWS tool for the job. You'll end out using the Codebuild setup we've given you but without this deployment step
Harness the power of AWS for hosting PHP-based websites and apps.
Idealstack is a powerful hosting console that creates a modern, autoscaling,
best-practice, AWS-native hosting cluster for PHP-based code in your AWS account